



Home | About Us | Contact Us | Threats to your Security on the Internet | Products | Support | Online Store

RCT's & RAT's
What are they?
How do I detect them?
How many are there?
What ports do they use?
How do I Remove?
Acid Shivers
Acid Shivers (modified)
Back Orifice
Baron Knight
Big Gluck
Blade Runner
Bugs
Deep Back Orifice
Delta Source
Devil
Doly Trojan
Deep Throat
Deep Throat v2
Executer v1
Executer v2
Girlfriend
Hack 'a' Tack
Master's Paradise
NetBus
NetBus 2 Pro
NetSphere
Sockets 'de Troie
SubSeven (Sub7)
Whack-a-mole (NetBus)
WinCrash
Additional Resources
Latest News
Recommended Books
Recommended Links
Recommended Software

Back Orifice
Back Orifice (aka BO) currently affects Windows 95/98 PC's.
The "server" portion is typically named ".exe". It would be found in the WINDOWS directory and is relatively small (about 122kb).
Port 31337 (by default) is used to establish its connection between the "client" and "server".
Once installed, it is rerun every time the computer is started by means of an entry under the "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices" branch in the Registry.
Who is Responsible?
Back Orifice was created by a group who call themselves "The Cult of the Dead Cow" (also referred to as the "CdC"). They're an organization, who've stated that their intentions are to bring to light, the lack of security and vulnerability in certain operating systems, typically Microsoft Windows and NT.
Recently, (in August '98) they unleashed "Back Orifice" (aka "BO") to the Internet, which offers anyone the ability to take total control of another user's PC without the other person knowing.
Provided below, is a picture of what the "client" portion of the software looks like. It's what the remote user would use to control your system. What could be easier than "pointing and clicking" your way through another users PC?
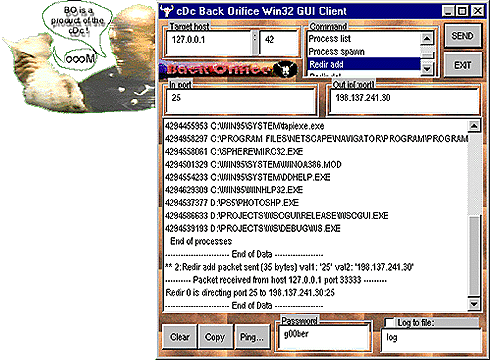
For further information, you can visit the CdC's website at www.cultdeadcow.com
How to Remove
The first five steps involve editing the Windows 95/98 registry. And although the steps are easy, I cannot be held responsible if a mistake is made. Please use caution.
Step 1.
Click START | RUN
type REGEDIT and hit ENTER
Step 2.
In the left window, click the "+" (plus sign) to the left of the following:
HKEY_LOCAL_MACHINE
Software
Microsoft
Windows
CurrentVersion
RunServices
Step 3.
In the right window, look for a key that loads a file called ".exe" (see NOTES below).
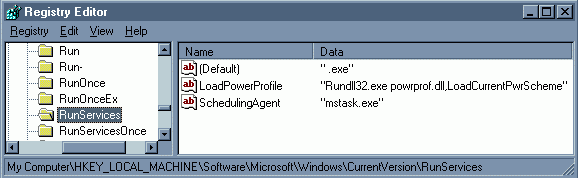
Step 4.
In the right window, highlight the key that loads the file and hit the DELETE key. Answer YES to delete the entry.
Step 5.
Exit the Registry
Step 6.
Reboot your computer
Step 7.
After the computer has restarted, open Windows Explorer
Step 8.
Go to the WINDOWS\SYSTEM directory and look for the ".exe" file (see NOTES below). It will NOT have a name to it, just an extension. Once you've found the file, DELETE it.
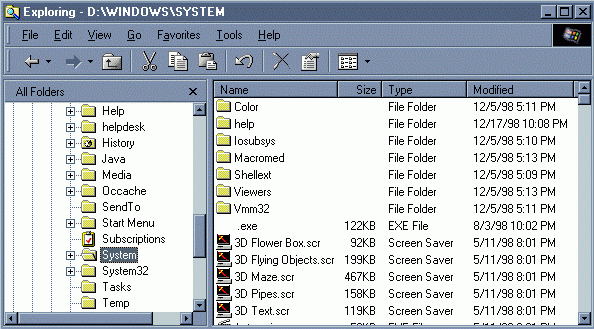
Make sure that your system is configured to show all registered extensions. Go to VIEW | OPTIONS and check the appropriate settings.
If extensions are hidden, it would look like this:
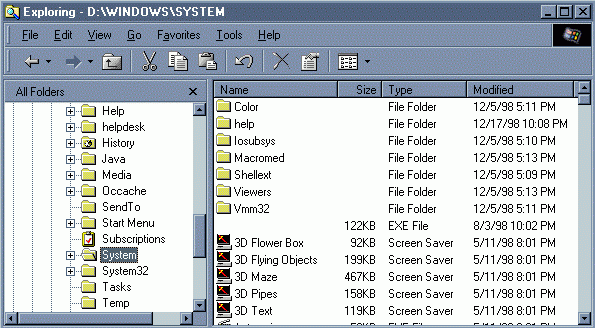
Step 9.
Also in the WINDOWS\SYSTEM directory, look for a file called "windll.dll". DELETE it as well. It's a file that's created by specifically by BO.
Step 10.
Exit Windows Explorer and reboot your computer.
Congratulations, Back Orifice has now been removed from your system.
NOTES:
As mentioned above, Back Orifice can also be installed with a file name other than the ".exe" name. By default, BO uses ".exe", but it can also be configured by the hacker to be anything. I know, because I installed it onto my own system to test this theory out. The ability to determine if BO has been installed with a name other than the default ".exe" name, is to carefully examine the RunServices section of the registry. Look for a key that launches a suspicious file. If you find a file that deserves closer inspection, look in the WINDOWS\SYSTEM directory for the same file name. If it's 122kb (or 123kb) in size, it's probably a renamed version of the "server" portion.
![]() Provided below are several screen shots exemplifying a modified Back Orifice. It's been configured to install the server portion as "shell.exe", enter the name of "Windows Explorer Shell" in the registry, as well as listen on UDP port 4000.
Provided below are several screen shots exemplifying a modified Back Orifice. It's been configured to install the server portion as "shell.exe", enter the name of "Windows Explorer Shell" in the registry, as well as listen on UDP port 4000.
Nasty, nasty, nasty...
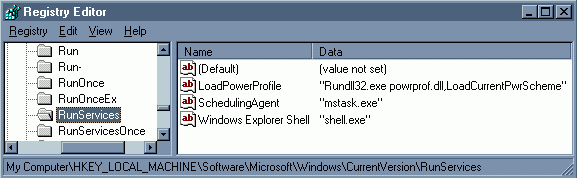
Above is a screen shot of its entry in the registry.
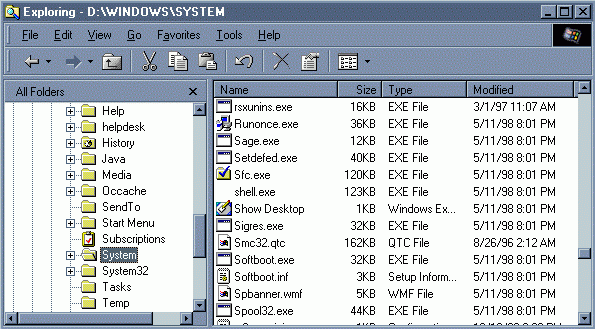
Above is a screen shot of its entry in Windows Explorer.
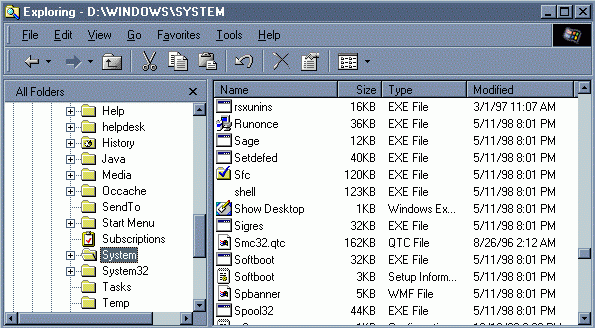
Above is a screen shot of its entry in Windows Explorer with extensions hidden.
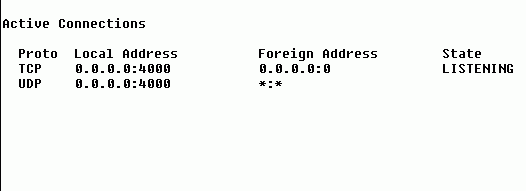
After using netstat, here's a screen shot showing BO "listening" on UDP port 4000.